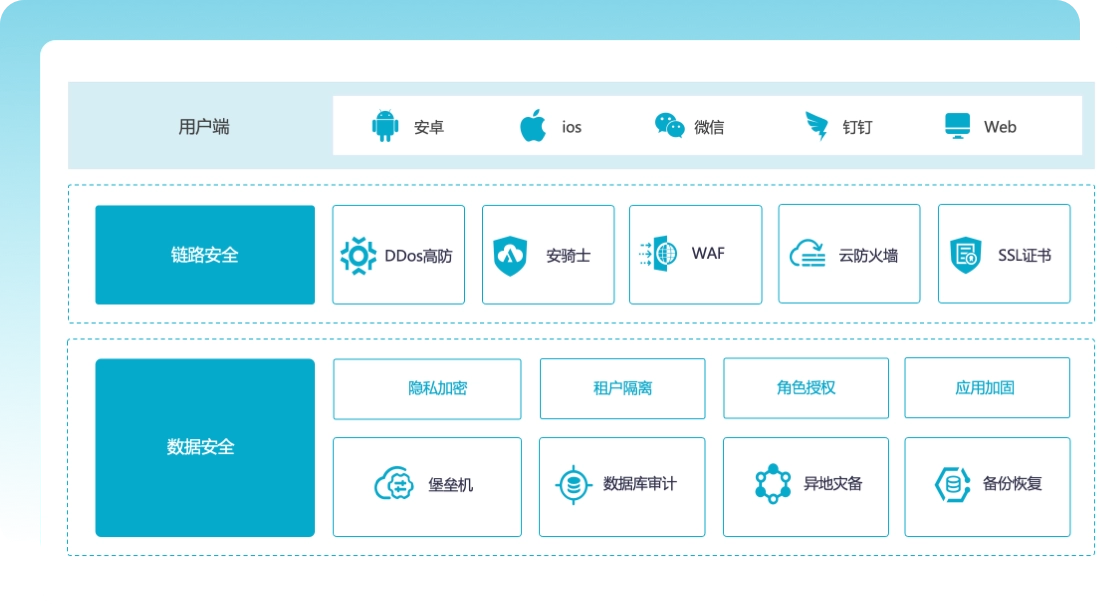
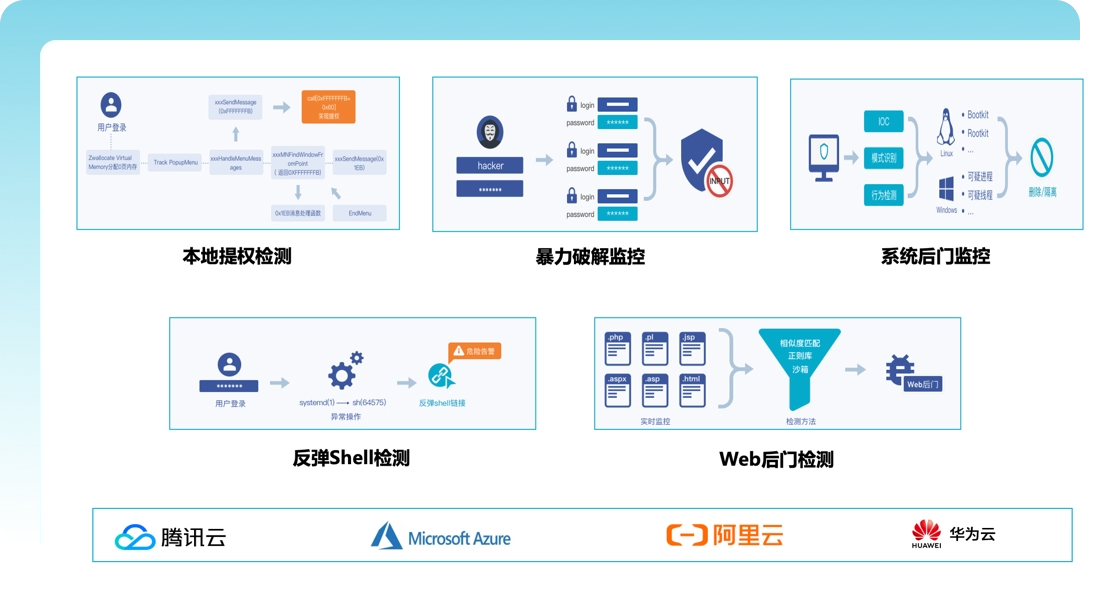
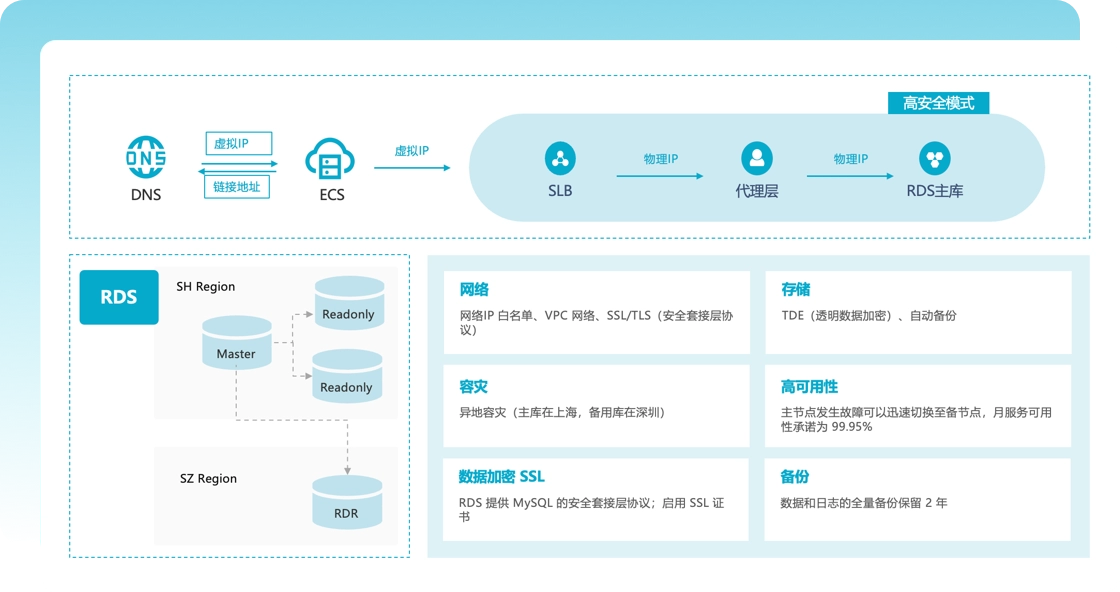
Data security protection
● Full-link encryption technology: Using the world's leading encryption algorithm to ensure the security of data throughout its entire life cycle from transmission to storage
● Data access control: A role-based permission management system ensures that data is only accessed by authorized personnel
● Data backup and recovery: Equipped with disaster recovery capabilities to ensure the security of data in emergencies
● Related certifications: Passed ISO 27001 Information Security Management System Certification and Level 3 Security Certification to comprehensively improve the level of data security protection
● Data access control: A role-based permission management system ensures that data is only accessed by authorized personnel
● Data backup and recovery: Equipped with disaster recovery capabilities to ensure the security of data in emergencies
● Related certifications: Passed ISO 27001 Information Security Management System Certification and Level 3 Security Certification to comprehensively improve the level of data security protection